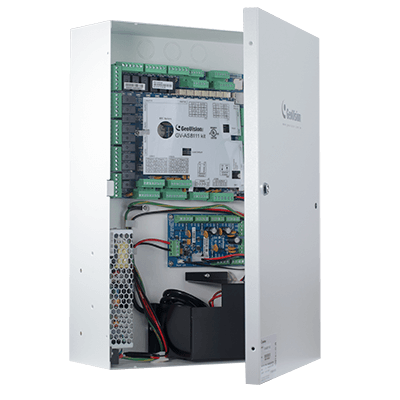
The security method of access control limits who or what can access resources in a computing environment. Bright Solutions has acquired knowledge and expertise in both logical and physical access control. Since they are aware of the importance of the key security principle that reduces risk to the company or organization.

Challenges
- The hurdle with access control is that it requires consistency to adequately encrypt information inside of a system.
- Opting for one of the accessible control models.
- Ensuring that the authorization controls are determined precisely for each personnel.
Solutions
- We used Role Based Access Control (RBAC) mode to restrict access of sensitive data from personnel whose roles do not necessitate it.
- Utilizing Multi-Factor Authentication (MFA) to ensure that only authorized users have the access to the encrypted data.
Usages
- An assessment or inspection of the current infrastructure.
- Developing a scheme for the system.
- Develop a system of automation.
- Put the strategy into motion.
- Analyzing the system’s components.
- Continue to enhance the solution.